For a while now I have had an idea in the back of my head to sort out a long standing issue. However due to the fact this has been and issue on a secondary network, and only affected myself (to which I had a easy work around as you will see), I have not pressed to hard to find the solution. However I had promised my self that after my exam last week I would sit down and sort it out once and for all.
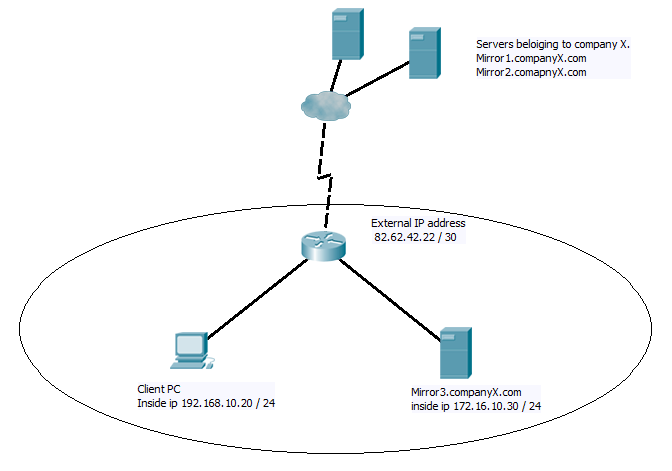
So here’s the situation, on a small network you have a client in one network, a web server in a second subnet and a single router acting as both the Internet gateway router, the firewall and handling all internal routing. Now this web server is of course accessible to the outside world as many web servers are. However the Domain name of the web server is not a domain I have control over. It is in fact a mirror of a 3rd party website. So they deal with all the DNS settings.
So of course the first thing to do is insure that outside users can connect in to the Webserver, and the internal clients can connect to the internet. So we require a basic NAT/PAT set up. Some thing along the lines of.
So far all straight forward. Outside users can get to the web server and inside clients can use the internet (assuming firewall rules and so forth allow it). But what happens if the inside client tries to go to the web address Mirror3.companyX.com? Well if we assume you have not set up an internal DNS zone for companyX.com. Then the internal client will use CompanyX’s DNS server, to resolve the name to the external IP address of the network 82.62.42.22, just as an outside user would. This create a problem, due to how the router processes the steps on NAT and Routing, it will not correctly forward the packets between the client and the server. Instead you will end up with a host unreachable error (if you want more detail what is happening please comment and I will add it in). So how can you allow the internal hosts to browse the web server then?
Well you have 4 (OK I am sure there are more 😉 but these are the main ones) solutions.
1. Simply point the client web browser to the internal IP address of the server. As I was almost the only person who ever needed to get to the server from the inside this was the method I have been using up until now. However this does not scale well, and neither is it pretty, so I knew there had to be a better way.
2. You could set up a DNS zone for companyX.com with a record for mirror3.companyx.com using it’s internal IP address . By pointing your internal clients to this DNS server they would pick up a rout able IP and browse the site. This is a standard method of DNS, and in many cases would be the preferred solution. However in this case it means setting up a Zone for a name you do not own. You also have to be careful to insure the inside clients can still resolve the mirror1 and mirror2 IP addresses. With out carefully planning this can get messy, especially if you have multiply mirrored servers from multiply domains.
3. Carry out NAT hair-pinning. This was original my first choice, and I do intend to come back to this as there are benefits to this method. But as I will cover also some issues with it. As I mentioned above trying to use the outside IP address of the server from the inside client results in issues to do with routing and NAT translations. Because the packets aren’t passing between the inside and outside the router can’t carry out correct NAT translations. However with a bit of cleaver configuration, and by using a loop back interface assigned to the NAT outside. You can with the use of multiply NAT statements and a static route get the router to pass the packet twice through the NAT algorithm and have it routed correctly. While this is a nice solution, its has the issue of huge CPU overheads for the router. Routing and the NAT has to be carried out in software with this method meaning that apart from in cases where there is very low traffic you need to be very careful if you implement this. (as I mentioned I will be covering how to set this up in a later post)
4. DNS re-writes! There is a not very well documented but very useful feature of NAT, called DNS re-writing, which does exactly what it says and by default is enababled. DNS response packets are checked by the router and any matching the NAT statements for the payload IP address will get re-written. However this will not work on PAT statements, only on pure one to one NAT. So the configuration above will NOT invoke this feature as it is. To get it working we need to add one more command.
Now with this command added the router will replace any IP address inDNS requests coming from outside the network that contain 82.62.42.22 with the internal IP address of 172.16.10.30. Now both the external users and the internal clients can use the same DNS server to resolve the address, and each will end up with the correct (but Different) IP address to be able to contact the web server.
To me solution 4 seems to be the neatest. Both companies keep full control of there networks and DNS settings, and there is much less over heads for the router to worry about. However note two issues.
First although we can still use PAT mappings on the IP external and internal address. So for instance where above we have a mapping set up “(config)#ip nat inside source static tcp 172.16.10.30 80 82.62.42.22 80 extendable” We could also have another mapping such as “(config)#ip nat inside source static tcp 172.16.10.40 22 82.62.42.22 22 extendable” Where SSH traffic goes to 172.16.10.40 and HTTP goes to 172.16.10.30. However any DNS request will use the plain NAT mapping so will always get replaced in the response with the 172.16.10.30 address in our set up. So you need to be aware of this and plan for it.
Second by using a NAT statement, all incoming traffic to any port will be translated through NAT. So you should insure that either an ACL or Firewall is blocking all traffic apart from what you want to come through.
So none are perfect but like with every thing in networking, you chose the one that fits best. And if you can’t find one, then your not looking hard enough. Or maybe you just need to invent a new method 😉
DevilWAH

Pingback: getting to the inside via the out side - TechExams.net IT Certification Forums