I decided that rather than just use other people labs I would come up with a few of my own, the following lab is very simple, requiring the enabling of EIGRP on two routers so they form a neighbour relation ship, and setting up which routes will be advertised. Followed by some simple summarization to reduce the size of the routing tables.
You can find the GNS 3 topology files HERE, these also contain the finalised configs if you want to see the method and commands used. (note you will need a 2691 image installed)
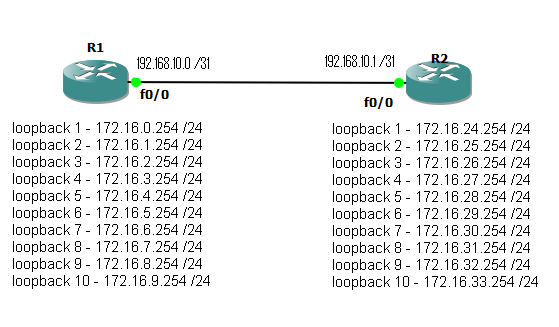
Fig 1
To start with we have two routers connected via a point to point link on interface Fastethernet 0/0. Each also has 10 loop back interfaces configured with various /24 networks configured.
The aim is simple, enable EIGRP with an AS number of 10, form a neighbour relationship between the two routers and update the routing tables so both routers can see / reach all configured networks. Ideal use as few network statements as possible, while remaining as specific as possible as to what networks get advertised. Autosmmorization should also be disabled.
After completing this, a #show ip route, should display something like this.
router1#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
192.168.10.0/31 is subnetted, 1 subnets
C 192.168.10.0 is directly connected, FastEthernet0/0
172.16.0.0/24 is subnetted, 20 subnets
D 172.16.32.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.33.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.28.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.29.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.30.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.31.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.24.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.25.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.26.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
D 172.16.27.0 [90/409600] via 192.168.10.1, 00:01:01, FastEthernet0/0
C 172.16.8.0 is directly connected, Loopback9
C 172.16.9.0 is directly connected, Loopback10
C 172.16.4.0 is directly connected, Loopback5
C 172.16.5.0 is directly connected, Loopback6
C 172.16.6.0 is directly connected, Loopback7
C 172.16.7.0 is directly connected, Loopback8
C 172.16.0.0 is directly connected, Loopback1
C 172.16.1.0 is directly connected, Loopback2
C 172.16.2.0 is directly connected, Loopback3
C 172.16.3.0 is directly connected, Loopback4
Now to reduce the size of the routing table we can manually summarise the routes. This is carried out under the interface that is sending out the update (in this case it will be fast ethernet 0/0 on each router). Again we want to be as specific as possible. The completed LAB uses multiply summarization statements , this increase the specificity of the summarization at the expense of adding an extra route in to the table. The routing table should now look something like.
router2#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
192.168.10.0/31 is subnetted, 1 subnets
C 192.168.10.0 is directly connected, FastEthernet0/0
172.16.0.0/16 is variably subnetted, 15 subnets, 2 masks
C 172.16.32.0/24 is directly connected, Loopback9
D 172.16.32.0/21 is a summary, 00:02:27, Null0
C 172.16.33.0/24 is directly connected, Loopback10
C 172.16.28.0/24 is directly connected, Loopback5
C 172.16.29.0/24 is directly connected, Loopback6
C 172.16.30.0/24 is directly connected, Loopback7
C 172.16.31.0/24 is directly connected, Loopback8
C 172.16.24.0/24 is directly connected, Loopback1
D 172.16.24.0/21 is a summary, 00:02:28, Null0
C 172.16.25.0/24 is directly connected, Loopback2
C 172.16.26.0/24 is directly connected, Loopback3
C 172.16.27.0/24 is directly connected, Loopback4
D 172.16.8.0/24 [90/409600] via 192.168.10.0, 00:02:26, FastEthernet0/0
D 172.16.9.0/24 [90/409600] via 192.168.10.0, 00:02:26, FastEthernet0/0
D 172.16.0.0/21 [90/409600] via 192.168.10.0, 00:02:26, FastEthernet0/0
So the routes from Router 1 are now summarized in to 3 blocks. 172.16.0.0/21 which would include the first 8 networks, plus the 172.16.8.0 and 172.16.9.0 /24 which fall out side the summarization.
Note also the routes to null that have been entered. When you set up a summarization, the router will automatically set up a route to null for that network. The reason for this is that you many not actually have routes to all the subnets for the network you have advertised as a summary. Imagen in the above case there was no loop back 5 and 6 on router 2, so no networks 172.16.28.0 and 172.16.29.0 /24. But the router is still advertising a summary address that includes them. When packet arrive at the router they are routed based on the most specific match. so a packet coming in with a destination address of 172.16.27.59 will match both the following routes.
D 172.16.24.0/21 is a summary, 00:02:28, Null0
C 172.16.26.0/24 is directly connected, Loopback
but because /24 is more specific than /21 the route to the loop back interface will be used. However if there is no more specific route, then the null route will be matched and the packets discarded.
OK I said it was simple and it is. The topology files have both the starting position and my completed example. This is of course not the only solution. You can argue there are neater ways to do it, but I chose to use multiply statements to show how specific networks can be picked and what happens when summary address do not exactly match the networks that are configured.
There will be one more EIGRP Lab coming up that will be more involved and included redistribution of static routes and manual formation on neighbours.
DevilWAH