Before getting in to the configuration of EIGRP, its worth knowing some of the fundamental workings of the protocol, why and from where it was developed and how it differs from the other protocols in offer.
The first thing to note about EIGRP is that it is a CISCO propriety protocol. So no matter how great it is, unless you have 100% kit, and you company allows non-standardised protocols to be used (many government organisation for example will not allow its use), then you will be unable to implement. But lets assume you do have 100% CISCO and your company allows EIGRP, should you use it?
EIGRP was CISCO’s a step along from IGRP, while IGRP was developed by CISCO as the step up from RIP. All are distant vector protocols where each routers receives a list of destination networks from each of its neighbouring routers, along with the cost to reach these networks. And from this information build a routing table that is used to route data packets by selecting the paths with the lowest cost to each destination.
EIGRP has several advantages on IGRP. First routes can be summarised at any interface on any router in the Autonomous system (more on AS’s in later posts), making it very flexible and truly a classless routing protocol. Secondly EIGRP runs DUAL ( Diffusing Update Algorithm ), Unlike most other routing protocols EIGRP learns not only the best path to a destination network but also any backup routes. So if there is a topology change, and a backup route exists it can be determined and activated in a very short space of time (milliseconds). Running DUAL also results in much lower processor overheads during topology changes and allows for not only load balancing across equal links, but also across unequal links (the only protocol to allow this). CISCO label EIGRP as an advanced distant vector protocol, as it benefits from many things found in link state protocols (loop free), while retaining the speed and simplicity of distant vector. It is also very simple to configure. Should you use it or not is a personal choice, however many of the networking experts in the field will agree with CISCO and confirm it is a very solid and efficient protocol to use.
EIGRP relies on 4 major components.
- Neighbour discovery and recovery.
- Reliability of transport of EIGRP management traffic.
- The DUAL finate state machine.
- The Protocol dependent model.
For neighbour discovery, Each router sends out periodic hello messages, when other routers receive these they check for compatibility and then reply. Once the neighbour relationship is formed updates containing routing data can be sent. One the initial updates have been exchanged and each router has the routing tables from its neighbour, the only updates that will be sent are for changed in topology. Other wise only hello messages are sent to determine the status of the relationship.
To keep traffic overheads down, EIGRP only uses reliable transport when needed. For example Hello messages may be sent as multicast with out reliability. Where as updates are sent as unicast with reliability. If it is to be used or not is determined by the originator requesting it in the packet.
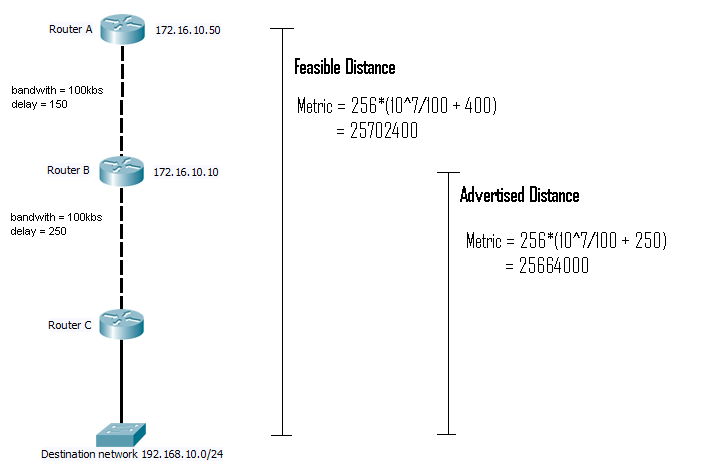
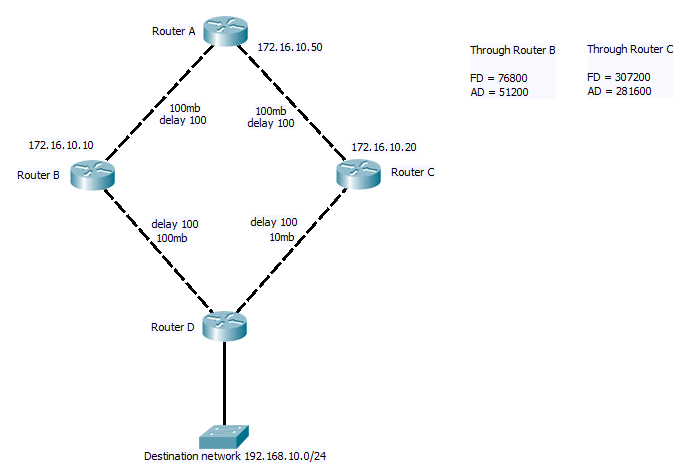
DUAL finite state machine. When DUAL is run on the neighbourhood table and Topology table (more about them later), it will pick the best cost path and add this to the routing table as the successor route. All other routes will be checked to see iof they match the requirements to be a Feasible successor, if so they will be marked as such. In the case of the successor failing, DUAL will pick the next best Feasible successor and add that to the routing table. This requires no re computation, if no Feasible successor can be found then it will query the neighbouring routers for the route.
The Protocol dependent module deals with network layer protocol specific requirements. EIGRP can route multiple protocols, it is the IP-EIGRP module that is responsible for IP routing.
EIGRP Tables.
There are 2 tables that are specific to EIGRP, the “neighbour table” and the “topology table”.
The Neighbour table contains a list of every neighbour that the router knows about, along with details of things like, address, interface, hold time, sequence numbers, and round trip times.
The topology table contains a list of all the learnt destination address, and for each router that has advertised the network, the advertised distant for the path, plus feasible distant, as well as the next hop router address. (It is worth noting that routers will only advertised links in actually use to an upstream router, feasible successors are not advertised if they are not involved in forwarding traffic)
DUAL runs on these two tables to form entries to the IP routing table that is used to forward data packets.
EIGRP Packet types.
- HELLO/ACK’s
- Updates
- Queries
- Reply
- Requests
Hello’s are sent generally as multicast, in an unreliably manor, the ACK (which is an empty hello message) is sent as unicast to the originator.
Updates that contain route information are usually sent as unicast, however updates that only contain link cost changes can be sent as multicast. Which ever method they are sent using the reliable method.
Queries are sent when a router loses the link to a destination and does now have a feasible successor in there topology, they will then queries all there connected neighbours to see if they have a path. Neighbours will reply is they have a successor to the destination, or if not will pass on the request to there neighbours. Queries are multi-case replys unicast, both are treated as reliable traffic.
Requests are sent to nebighour routers to request specifice information (route server applications), they can be both multi-cast or unicast and are always set as unreliable.
Route tagging and Route states.
EIGRP is aware of internal and external routes, routes can be tagged to allow passing of information between EIGRP AS’s or when redistribution occurs between different routing protocols. (we will come back to tagging later) This allows from more controlled policy based routing.
Routes in EIGRP can be in one of two states. Passive which is good and means a route is stable in the topology. and Active when the router is forming a re-computation on the route. This would happen where there is no feasible successor and the router is having to query neighbouring routers. Ideally routes should almost never be in the active state.
Further reading
Eigrp intro cisco
Internetworking Technology Handbook EIGRP
Next time we will explore some of the terminology of EIGRP before running through the more common configuration and verification commands.
DevilWAH