I remember searching around for ages looking for this solution a few years back, so I thought I would share it with you. Bear in mind that there are much more secure solutions around, such as 802.1x port based authentication. However these require a lot more setting up, not to mention the kit to support it. For what it is “Lock and Key” is one of these ideas that does exactly what it says on the tin..
So what exactly is it that “Lock and key” does any way. The idea behind it is to allow you to on demand open up access between subnet / networks. May be it is clearer if we look at the following digram.
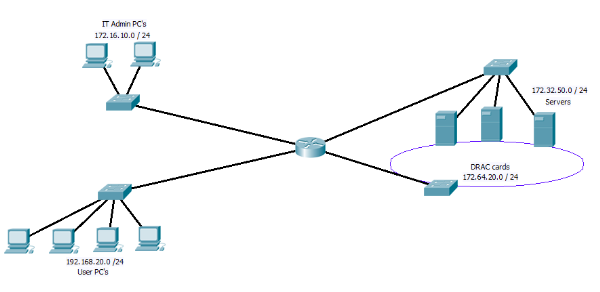
Figure 1
In Figure 1 we have the IT PC’s, the users PC’s, the servers and the DRAC cards all on separate networks. If you have not come across DRAC cards before, they are an additional card that can be fitted to Dell servers, that have there own redundant NIC, if the server should crash, you can connect to the DRAC card and force a hard reboot among other things. Very useful for remote management of server! However as you can image not some thing you want to allow users near!!
So looking at the digram above you may place an access list on the incoming traffic from the user network (192.168.20.0) to block any access to the DRAC network. While leaving the IT admin PC’s able to reach them. But what happens if you are at a users PC, the server has crashed and you need to reboot it? This is where the “Lock and Key” idea come in.
By using a dynamic Access list along with the user name auto command. you can on the fly open up the blocking access list you have created to allow the PC you are working on have access to the Drac network.
First we need to set up the a dynamic IP access list under global config, remember this access list has to be applied to the interface connection to the user PC’s, we will be applying it in the “in” direction.
ip access-list extended Lock-key
dynamic Dracacess timeout 60 permit ip any 172.64.20.0.0 0.0.0.255 log
deny ip any 172.64.20.0 0.0.0.255
deny ip any 172.16.10.0 0.0.0.255
permit ip any any
So before “lock and Key” is active users are prevented from accessing the IT unit PC’s and the Drac network, but have access to every thing else.
Next we set up the user we are going to use as the “Key”
username Dracs secret CISCO
username Dracs autocommand access-enable host timeout 15
So here we set up the user Drac and add the auto command to run when they log in. The 15 minute time out here is the idle time out. However as we have set an absolute time out above in the access list its self, this will log out the user after 60 minutes if they are active or not.
Lastly we need to go in to the interface that faces the users network and assing the Access list, and set the VTY line for telnet access and to use the local user database. so from global config again.
interface <ID>
ip access-group Lock-key in
exit
vty 0 15
transport input telnet
login local
exit
Now to use it is simple, from a users PC start a telnet session with the router, at the user name and password prompt users the user name of Drac and password configured. The connection will be droped by the user but you an extra line will be added to the access list along the lines of.
permit ip host xxx.xxx.xxx.xxx 172.64.20.0.0 0.0.0.255 log
Any you user PC now has access as long as it is sending data or until the limit of 60 minutes.
Of course you may not like using telnet and it is possible to use SSH (but then the user PC needs a ssh client installed), you can also change the port that the router listens for telnet or SSH on a VTY line. You can also apply the auto command to the VTY line so any one who logs on through that VTY line will trigger the lock and key. If you do this then you will need to set up some VTY lines to use one port with the autocommand config, and some other VTY lines to use a different port with out the autocommand. Other wise you will not be able to mange the router!!!
This Link covers some more examples.
As I said at the beginning there are much better ways to do this, 802.1x as i mentioned is just one of them and some thing I will cover in more detail soon. But for a small/medium size networks, where cost is an issue, but you still want to add an extra bit of security. They are a nice way to restrict users, while allowing network admins to carry on working efficiently away from there desks.
DevilWAH